Share this
The 4 Cloud Security Vulnerabilities The NSA Wants You To Watch Out For
by Serena Raymond on Feb 5, 2020 12:00:00 AM
Cloud security was big in 2019, and it’s no wonder when you look back at data breaches that impacted “cloud-first” companies like Capital One. According to Flexera’s 2019 State of the Cloud Report, 94% of enterprises are already in the cloud. This begs the question: How can companies of all sizes mitigate cloud vulnerabilities?
Last month, the NSA released guidelines for addressing cloud security vulnerabilities. Their advice to anyone using cloud applications is to evaluate the risk. This means customers should be aware of the various underlying cloud architectures, who the main threats are, and which security vulnerabilities they need to prepare for.
A Cloud Service Provider (CSP) is any cloud-based service such as Amazon Web Services, G Suite, or Adobe Creative Cloud.
As the customer of a CSP, you have to be aware of the risks associated with the cloud and the actions you can take to reduce those risks.
Cloud Architecture
There is no standard architecture for CSPs. That means, there’s no standard way to stop threats as some architectures are inherently more secure than others.
The big takeaway here is you’ll want to ask your cloud provider what architecture they use. Ask them what the drawbacks are to that architecture and what responsibilities you need to take on to equip your organization with the right type of security.
Cloud Encryption and Key Management
CSPs provide their own encryption or key management (i.e. making your data unreadable if it gets into the wrong hands), but there are also third party alternatives available. You might choose to go with the CSP’s built-in encryption services since it’s designed to integrate with other cloud services. It also reduces the amount of work your team needs to take on.
However, going with a third-party encryption service can protect you in the event your CSP’s built-in securities fail.
Cloud Security Responsibilities
It’s up to the customer to determine which responsibilities will belong to which party (the CSP or the customer of the CSP), and which of these responsibilities are shared. This is going to impact day-to-day of your organization as well as how much trust you’re putting into your CSP.
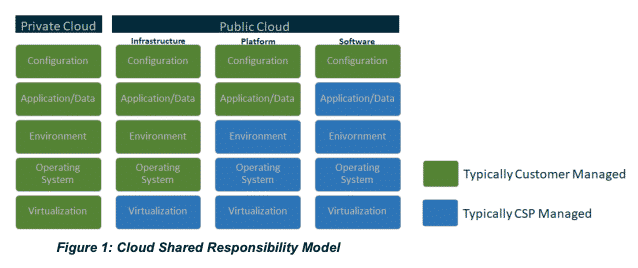
You and your CSP should share the following responsibilities:
- Threat detection
- Incident response
- Patching and updates
Who’s Behind The Threats?
The NSA identified four “Cloud Threat Actors” in their report. Those are the ones responsible for intentionally or unintentionally compromising data. They are:
- Malicious CSP administrators
- Malicious customer cloud administrators
- Cyber criminals (including nation state-sponsored crime)
- Untrained or neglectful customer cloud administrators
❗Note three out of four of the Cloud Threat Actors are insider threats and not outside malicious organizations. In reality, you’re not always protecting yourself against that anonymous outsider. You need to put the right security in place to make sure information isn’t compromised because of what people on the inside do (or don’t do).
Make sure you’re constantly evaluating your internal security and asking these types of questions:
- Who has access to this (and do they need access)?
- Is two-factor authentication set up?
- Is this data encrypted?
- What other cloud services does this resource integrate with?
It’s a lot easier to fight outside threats when your house is in order to begin with.
The Four Cloud Security Vulnerabilities
So what are the four biggest cloud vulnerabilities, and what can you do to mitigate them?
1. Misconfiguration
Misconfiguration is one of the most common cloud vulnerabilities, and it’s unfortunately relatively easy to exploit.
The biggest culprit of misconfiguration is a misunderstanding of the cloud service policy. To prevent misconfiguration, make sure you follow setup procedures correctly and create alerts if something becomes misconfigured. These controls need to be dynamic in order to keep up with changes as they occur—and they will.
2. Poor Access Control
Weaknesses in access control occur when authorization or authentication methods are easily bypassed. Think about your co-worker who forgot to set up two-factor authentication on their email and their account wound up compromised. Or your dad telling you his bank password is “Chase123.”

If you get serious about owning this vulnerability, it’s going to be a lot easier to keep your data secure. Reset passwords regularly, and make sure they pass a password strength test.
3. Shared Tenancy Vulnerabilities
This threat is rare, but you still need to be prepared for it. Cloud services use various hardware and software to create their offering. This vulnerability occurs when someone can identify those internal softwares and exploit them. As an example, an external threat might discover a certain CSP uses hardware that has flaws in the chip design and exploit that. Or, if someone can get into a single container, they might be able to get into other containers that are on the same server.
Work with your CSP and find out if their service has been evaluated with National Information Assurance Partnership protection profiles in mind. You’ll need to work together to make sure you’re protected.
4. Supply Chain Vulnerabilities
This rare vulnerability occurs when there is an insider threat, or when someone leaves an intentional “backdoor” in a piece of software used in a CSP so that it can be exploited by future threats.
It’s up to the CSP to protect their customers from this threat. However, leveraging secure coding practices and making continuous security improvements are just a couple of steps you can take to help mitigate risk.
Cloud Security And You
When it comes to the most common cloud vulnerabilities based on the NSA’s recent guidelines, it’s up to CSP customers to know the risks and protect themselves. The most important aspects of preventing security leaks are implementing tight authorization controls and following CSP configuration guidelines. Focusing on internal threats (the most common) will set you up for cloud security success in the long run. Get the full NSA guidelines here.
How can DNSFilter help you fight security threats? We keep organizations like yours safe from phishing attacks and suspicious domains with our AI-powered classification. See for yourself when you sign up for a free trial.
Share this
 Artificial Intelligence in Cybersecurity
Artificial Intelligence in Cybersecurity
The term “artificial intelligence (AI)” was first coined in 1956. While progress stalled for many years, we can thank IBM for sparking real interest in AI as viable technology: First in 1997 when the computer Deep Blue defeated a chess champion and again in 2011 when Watson won Jeopardy!
 The Mind Games Behind Cyber Attacks
The Mind Games Behind Cyber Attacks
Hackers have long understood that the most sophisticated firewall is no match for a well-placed psychological trick. While many focus on the technical prowess of cybercriminals, the real magic often lies in their ability to manipulate human behavior. By exploiting our natural tendencies and cognitive biases, hackers can slip past even the most robust security systems. It's not just about cracking codes; it's about cracking the human psyche.
 AI and Cybersecurity Risks: Why DNS Filtering is Critical for AI-Driven Workplaces
AI and Cybersecurity Risks: Why DNS Filtering is Critical for AI-Driven Workplaces
Artificial intelligence is transforming business operations, automating everything from customer service to data analysis. But with these advancements come new security challenges. AI-driven cyber threats are becoming more sophisticated, enabling attackers to automate phishing campaigns, generate malware, and exfiltrate sensitive data at scale. Without proper safeguards, AI tools can unintentionally leak corporate secrets or connect to malicious ...


