Compliance ≠ Security: Healthcare Organizations’ Biggest Threats
by Rebecca Gazda on Jul 26, 2022 12:00:00 AM
Compliance and security are not the same. And in healthcare, this difference is incredibly important. Checking off compliance boxes will not ensure patient data is fully secure.
It is a start, sure. But true security in your organization requires much more than compliance standards might suggest.
Security and Compliance in Healthcare: What’s the Difference?
Compliance is the first step to achieving security. Healthcare compliance can be defined as the ongoing process of meeting or exceeding the legal, ethical, and professional standards applicable to a particular healthcare organization or provider. This is especially important for healthcare organizations because the data they possess is classified as Protected Health Information (PHI) under HIPAA.
Security is the product, solutions, and/or process in place to do the work. A secure organization not only follows all of the rules outlined by the compliance guidelines, but also:
- Ensures there are no gaps in security
- Trains all employees in what they can do to maintain security
- Ensures that all possible use cases are covered
To simplify: Compliance is the checklist. Security is the ongoing, ever-evolving process.
Special Considerations in Healthcare Security
Healthcare organizations have to protect the most vulnerable and personal types of information. If they are affected by an attack, real human lives can be at stake.
However, healthcare organizations can struggle with training a workforce made up of vastly different backgrounds, technical skill levels, understanding of cybersecurity, and willingness to comply with cybersecurity guidelines.
DNSFilter Healthcare Customer Data
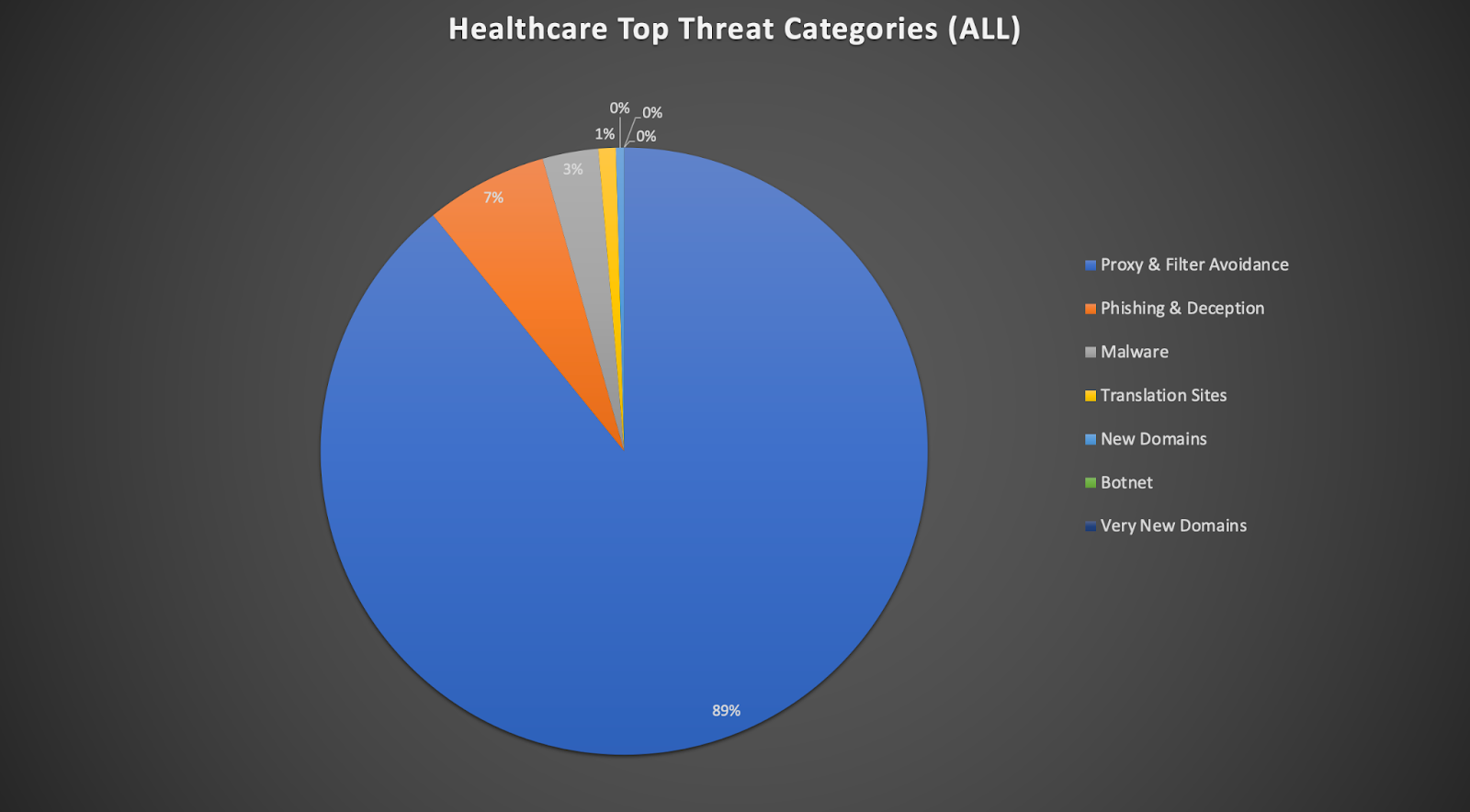
Looking at data collected from DNSFilter healthcare customers in the past month, the highest threat category encountered was Proxy & Filter Avoidance. Proxy & Filter Avoidance are sites that provide information or a means to circumvent DNS based content filtering, including VPN and anonymous surfing services.
For healthcare organizations, the biggest threat seen in DNS queries is employees trying to get around DNSFilter and other security tools. This speaks volumes to the need for more training and clarification around what cybersecurity tools are in place, and why they are necessary.
Also visible in this data:
Defined as: Fraudulent websites that aim to trick users into handing over personal or financial information. Phishing and deception websites can open up a “can of worms.”
If employees click the links inside of them, they open the organization up to malware, ransomware, botnets, and personal login information being stolen and used.
Defined as: Malicious software, including drop servers and compromised websites, that can be accessed via any application, protocol, or port. This also includes drive-by downloads and adware.
A huge issue here is ransomware attacks. Healthcare providers are much more likely to be forced to pay a ransomware attacker to get their data or systems back online because literal lives may be at stake.
- Translation Sites
Defined as: Sites that perform translation from one language to another, usually performed by a computer. May also be used as a means to circumvent content filters.
- New Domains
Defined as: Domains which have been registered in the last 30 days. These have a high probability of serving malicious resources.
- Botnet
Defined as: Command and Control botnet hosts. Prevents receiving commands for already infected machines and also helps to identify infected machines.
- Very New Domains
Defined as: Domains which have been registered in the last 24 hours. These have a high probability of serving malicious resources.
An Education Problem, and also a Configuration Problem
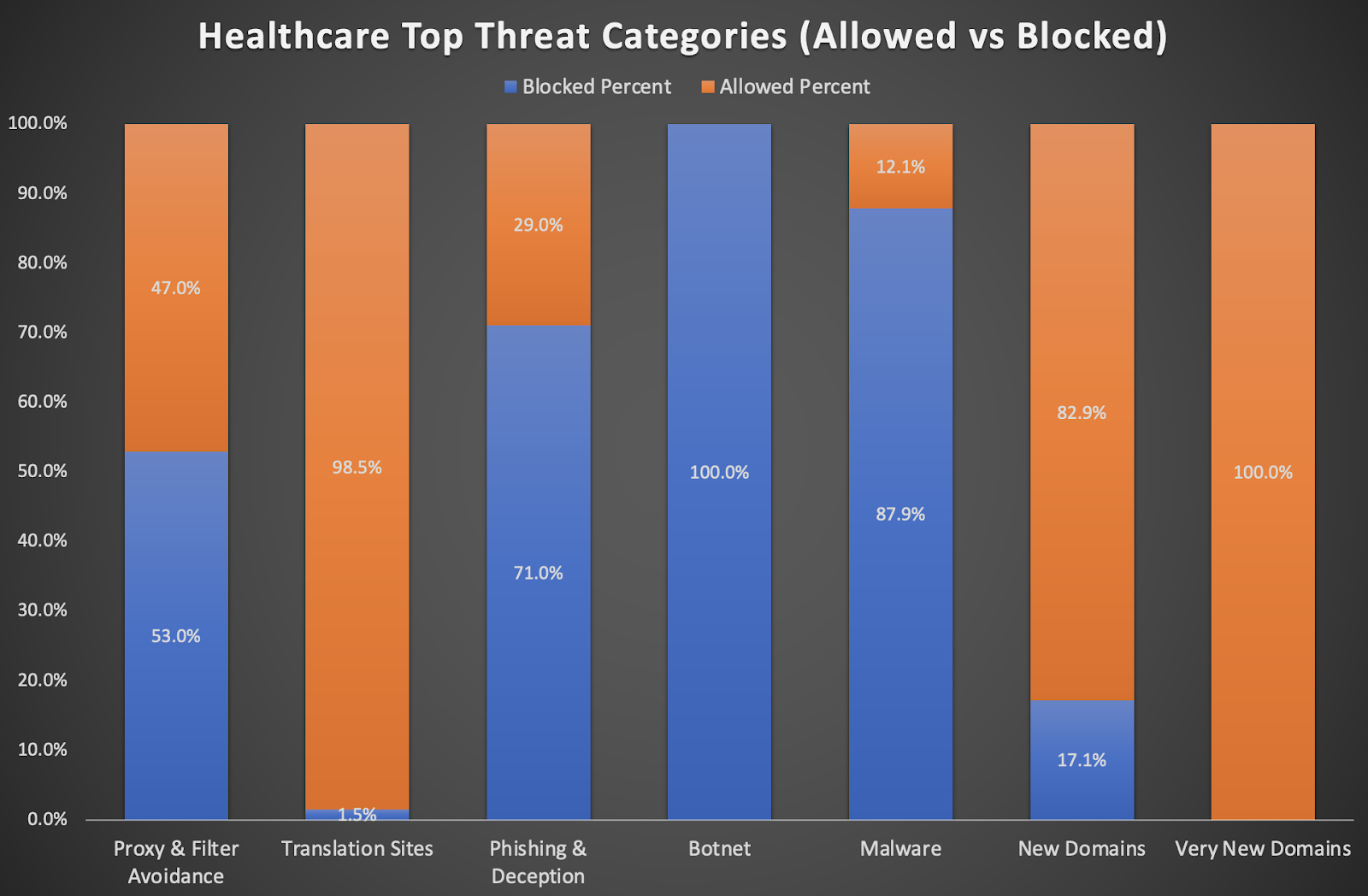
Digging deeper into the data from above, it’s clear that healthcare threats are not only an issue of employees clicking the links, but also an issue around security measures that are put in place by administrators.
Of the threats identified above, not all were blocked by DNSFilter because some customers have opted not to block all security/threat categories. Of course, this is an organizational choice.
However, DNSFilter advises caution and urges organizations to take careful consideration around the policies created within our tool.
 6 Security-Focused New Year’s Resolutions for 2026
6 Security-Focused New Year’s Resolutions for 2026
The start of a new year is the perfect time to reset habits—not just personal ones, but digital habits too. Cybercriminals don’t need zero-days or nation-state tooling if we keep handing them easy wins through reused passwords, oversharing, and rushed reactions.
 Inside Business Email Compromise Scams: How to Protect Your Business
Inside Business Email Compromise Scams: How to Protect Your Business
The Scam That Outsmarts Awareness Training
It starts with a routine email.



