Share this
How to Block Unwanted Websites On The Company Network
by Serena Raymond on Mar 11, 2021 12:00:00 AM
How to block unwanted websites
DNS security with content filtering is the best way to block unwanted websites on the company network. Unfortunately, it's all too easy to trick people into clicking links they shouldn't. That means, even if someone is cybesecurity aware or careful about what they click on, they can still find themselves on an unsavory or malicious site.
When you use a DNS security solution like DNSFilter, you’re able to:
- Control what site categories users can access
- Apply block and allow lists
- Block entire threat categories such as phishing, malware, and botnet threats
- Look at DNS queries on your network to see if any unwanted sites are slipping through the cracks
Block lists vs. categories
It’s possible that you have a set list of websites that you know you want to block. You might even already have that list. It’s easy to upload that list to DNSFilter’s Block List tab under the filtering policy you create.
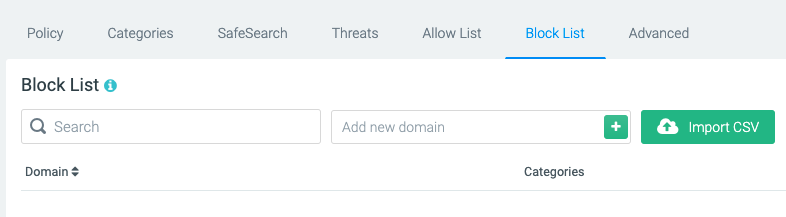
But blocking categories is much simpler. Categories are buckets that domains fall into. A domain can be labeled as more than one category. For instance, Facebook is categorized as both “Social Networking” and “Business.” DNSFilter has nearly 40 categories to choose from and 7 threat categories. Blocking website categories allows you to apply blanket policies to your end users. But you can also pair blocking certain categories with either block or allow lists. So if you want to block Social Networking but still allow LinkedIn access, you can do that.

The easiest way to get started with content filtering is to deploy the DNSFilter Roaming Client. The Roaming Client enables you to block (and allow) websites on an individual device as opposed to deploying across a network. Using the Roaming Client only a few minutes to get set up.
Here’s what you need to do:
- Sign up for a DNSFilter account
- Set up your site (Hint: This is your business’ location)
- Create your first policy under the “Policies” tab
- Install the Roaming Client by navigating to Roaming Clients → Install
- Apply your policy
Choosing the right deployment method
But Roaming Clients aren’t right for everyone. If you’re working in a traditional office, or provide public WiFi, you need to ensure that anyone who connects to your network is protected from deceptive sites. And you can’t install the Roaming Client on a stranger’s device!
But what you can do is deploy DNSFilter via your company network or via our Relay.
If you just want to apply content filtering to your office’s internet with as few frills as possible, the network deployment will work best for you.
Our Relay is a virtual appliance that will give you greater visibility into your network DNS traffic. A normal network deployment will show you the queries being made on your network, but it won’t be able to tell you which device is sending which query. The Roaming Client allows you to do that because of the way it’s implemented, but the Relay also allows you that visibility.
If you need to handle local domains, you’ll find our Relay useful. You can configure the Relay to recognize queries for local domains and forward those queries to your internal DNS resolver while sending all other queries to DNSFilter.
But...why should you block websites?
There are plenty of reasons why you might want to block employees from certain sites. You might be worried about time wasters—the internet has plenty of those. We’re constantly online, and more employees are working out of web applications than ever before. Unfortunately, a byproduct of spending more time online for work means there are more distractions than ever before. Blocking site categories such as social media, gambling, and gaming can give employers peace of mind that their employees are spending time actually working.
Maybe you’re concerned with threat protection. So many sites seem legitimate but turn out to be phishing or malware sites that can turn into an IT headache—not to mention a costly data breach. It is getting harder and harder to tell a real site from a fake one.
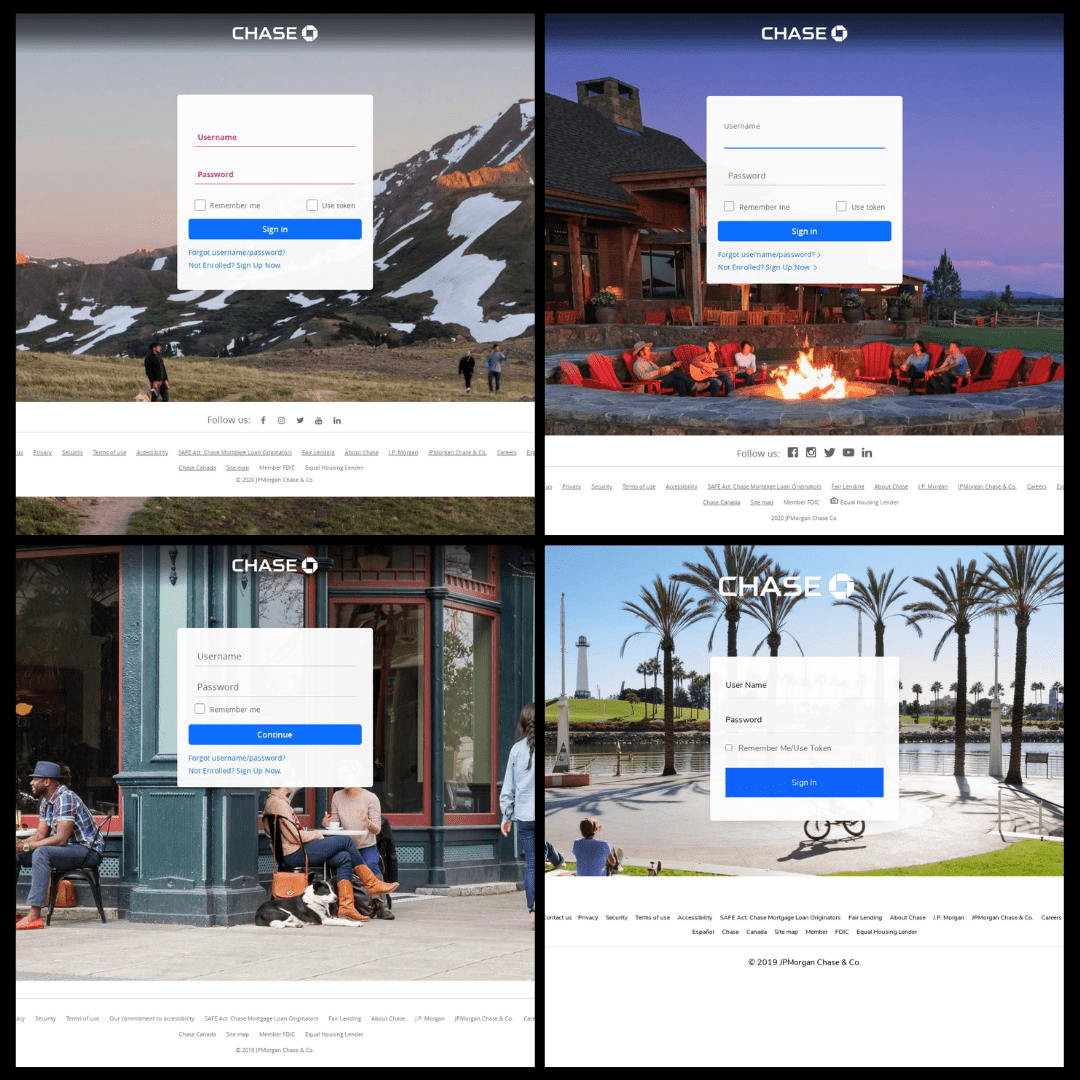
For the record, none of those logins are real. They are all completely fake.
Hackers use tactics such as typosquatting, where they claim domains close to the one they’re impersonating. For instance, if they’re creating a fake Chase login page they might register chhase[dot]com and set up a fake login. It’s the same reason a lot of brands will register domains that include brand typos in the name. It’s to keep hackers at bay and protect their brand.
Blocking known malicious sites (and having the ability to scan sites in real-time) is one of the best ways to mitigate risk.
Finally, we find a lot of people want to block unwanted websites because they want to achieve NIST compliance or CIPA compliance. Some companies may have their own internal compliance regulations for HR or other purposes that lead them to seeking out ways to block content online.
Ready to start blocking unwanted websites? Get your free trial.
Share this
 Artificial Intelligence in Cybersecurity
Artificial Intelligence in Cybersecurity
The term “artificial intelligence (AI)” was first coined in 1956. While progress stalled for many years, we can thank IBM for sparking real interest in AI as viable technology: First in 1997 when the computer Deep Blue defeated a chess champion and again in 2011 when Watson won Jeopardy!
 The Mind Games Behind Cyber Attacks
The Mind Games Behind Cyber Attacks
Hackers have long understood that the most sophisticated firewall is no match for a well-placed psychological trick. While many focus on the technical prowess of cybercriminals, the real magic often lies in their ability to manipulate human behavior. By exploiting our natural tendencies and cognitive biases, hackers can slip past even the most robust security systems. It's not just about cracking codes; it's about cracking the human psyche.
 AI and Cybersecurity Risks: Why DNS Filtering is Critical for AI-Driven Workplaces
AI and Cybersecurity Risks: Why DNS Filtering is Critical for AI-Driven Workplaces
Artificial intelligence is transforming business operations, automating everything from customer service to data analysis. But with these advancements come new security challenges. AI-driven cyber threats are becoming more sophisticated, enabling attackers to automate phishing campaigns, generate malware, and exfiltrate sensitive data at scale. Without proper safeguards, AI tools can unintentionally leak corporate secrets or connect to malicious ...


