How To Prevent Phishing Attacks
by Serena Raymond on Feb 16, 2021 12:00:00 AM
In 2019, 88% of organizations around the world that were surveyed were the target of a spear phishing attack. With the rise of phishing attacks in recent years, malware has taken a back seat. Hackers are less interested in deploying malicious code to devices and much more interested in gaining login credentials and sensitive information. That's why it's becoming absolutely vital that organizations understand how to prevent phishing attacks.
Types of phishing
Most people are familiar with email phishing. You get an email from someone you know or a company that you're a customer of asking you to take some sort of urgent action. CEO fraud is an incredibly common form of email phishing. It's where a party pretends to be the CEO of a company and targets an employee with the goal of getting them to take some sort of action that would allow the deceptive party to benefit. But phishing isn't just done via email.
A major component of most phishing campaigns is a phishing website page. For instance, at DNSFilter we see fake Chase login pages, like this one, weekly:
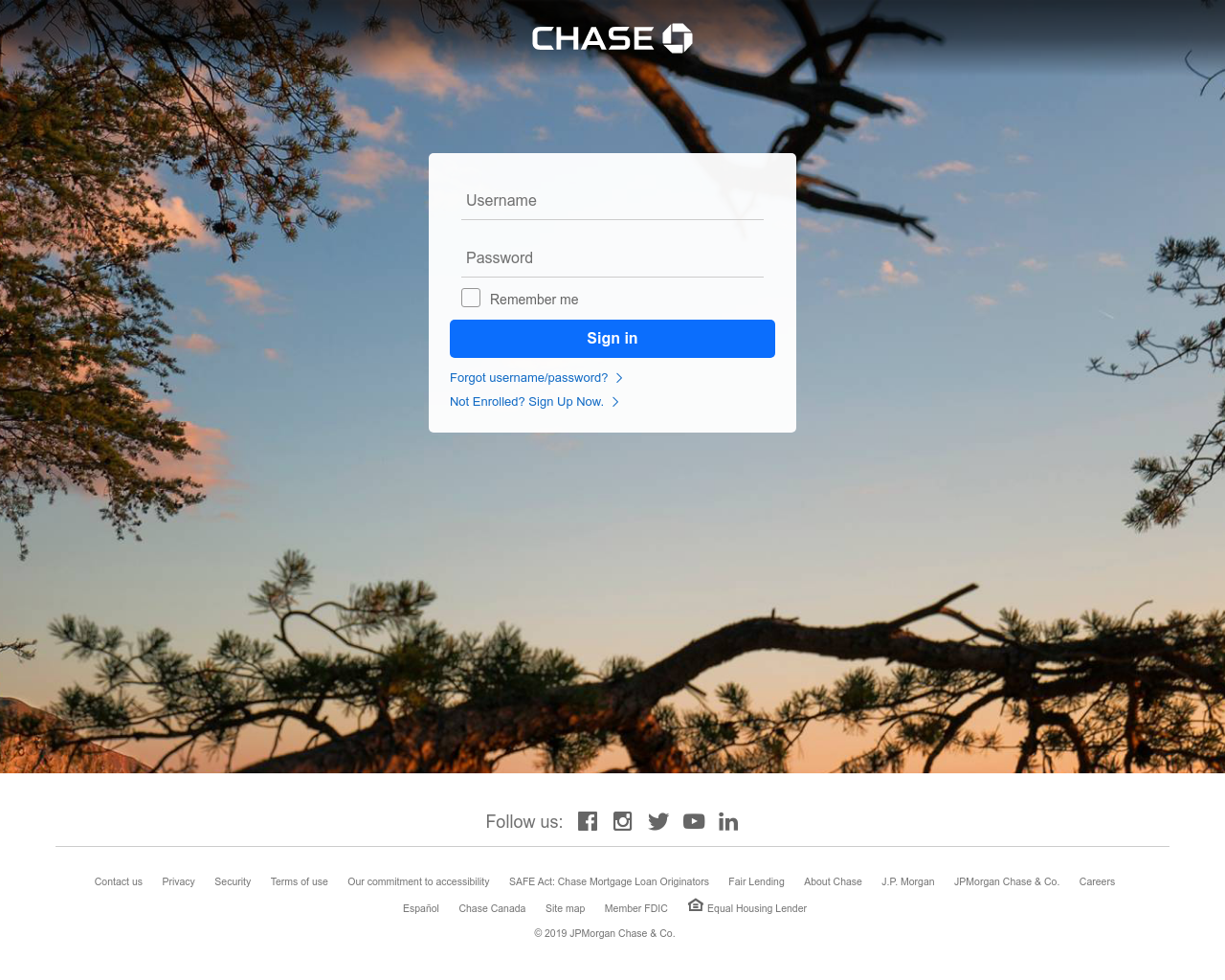
This type of mimicry is known as "website spoofing" or "domain spoofing." But other phishing pages may be acting as a completely fake company without any imitation.
Phishing websites like the one above might be found in emails (as mentioned above), malicious ads, search results, or even linked from trustworthy pages.
But phishing can also occur via phone calls. This is called vishing, as in voice phishing. Similarly, phishing via text messaging is known as smishing (SMS phishing).
While a lot of phishing attack attempts are engineered to be deployed as broadly as possible, spear phishing campaigns are highly targeted. The hacker is likely interested in targeting a particular company and will scrape information from the company website and target active employees into handing over sensitive company information. There can be a lot of range in how a spear phishing attack appears, but overall these attacks are highly customized.
You might have also heard of the term "whaling." Whaling attacks are even more customized spear phishing attacks. While spear phishing attacks usually target lower-level employees, whaling goes after "big phish." That means hackers are targeting the C-suite. They might impersonate partners, major banks, or large customers.
How to recognize phishing
In order to prevent phishing, it's important to know how to recognize it. There are a few key things to look for. If something strikes you as suspicious ask yourself these questions:
- Is this the type of email message this person would send me?
- Would this person send me an email about this topic, or would they use another form of communication?
- Does the "sender" of this email match the actual email address?
- Are there strange typos throughout this email or page?
- Is this the website I expected to see after clicking that link?
- Does the URL of this page match the page content?
- Is this the login page I'm accustomed to seeing?
- Am I being promised something that seems too good to be true?
If anything ever seems questionable, treat it as phishing until proven otherwise.
To the point: here's how to prevent phishing
Yes, phishing is everywhere. It's customized. And it's well-orchestrated. So what actions can you take to prevent phishing attacks?
Education
For any type of cybersecurity prevention measures, education will always (and should always) be at the top of the list. Educate your employees. The ability to recognize a phishing attack in the wild is the first step in preventing them completely. Building a cybersecurity-aware culture needs to be built on education. Employees should feel empowered to report threats and question if an email is legitimate or a phish.
Filter out threats on your network
By enabling DNS protection, you can filter out phishing sites altogether. That means if an employee opens and clicks on a phishing email, the link in the email won't work.
At DNSFilter, we have 7 threat categories including "Phishing & Deception", which we define as "Fraudulent websites that aim to trick users into handing over personal or financial information." Blocking these websites is an obvious step in preventing phishing attacks.
Domain greylisting
Phishing sites are generally set up on newly registered domains. And they're likely taken down early on in the domain's life as people catch onto the fact that these sites are a threat. That's where domain greylisting comes in.
Domain greylisting is the act of blocking newly registered domains to protect users from possibly malicious sites. With DNSFilter, you can block domains for the first 30 days after they've been registered. This is generally enough time for a domain to be discovered as a threat and subsequently taken down.
What if an employee gets phished?
If someone at your company has been phished, they need to change their passwords. They should also do an anti-virus scan in case this phishing attack deployed some sort of malware.
Finally, and most importantly, they should inform the security point person at your company. This way, they can alert other employees to watch out for phishing schemes like this and to do a more thorough investigation into if this was a spear phishing campaign. They might also choose to take additional actions both to safeguard information lost and protect employees in the future. After all, each phishing attempt is also an educational opportunity.
How to report phishing
If you've encountered a phishing attack, there are a few places you report the attack to, you should let CISA know if you're in the US. You can also contact the Anti-Phishing Working Group (APWG).
As a DNSFilter customer (or trialist), if you've found an unblocked phishing site you can also submit it to us so that we can block the domain through our Domain Lookup tool. In Domain Lookup, type in the domain in question, and select "Report threat" if it is not already listed as a threat.
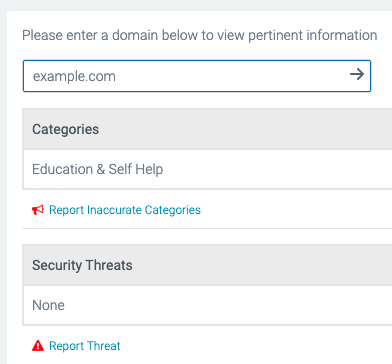
Not only will this help other DNSFilter customers, but this will also enable our AI to continue to learn about new threats so it can recognize them before you do.
For more on phishing attacks, download our whitepaper The Price of Phish.
 6 Security-Focused New Year’s Resolutions for 2026
6 Security-Focused New Year’s Resolutions for 2026
The start of a new year is the perfect time to reset habits—not just personal ones, but digital habits too. Cybercriminals don’t need zero-days or nation-state tooling if we keep handing them easy wins through reused passwords, oversharing, and rushed reactions.
 Inside Business Email Compromise Scams: How to Protect Your Business
Inside Business Email Compromise Scams: How to Protect Your Business
The Scam That Outsmarts Awareness Training
It starts with a routine email.



