Share this
A Statement on the Kaseya Ransomware Attack
by DNSFilter on Jul 6, 2021 12:00:00 AM
Just before US offices closed for the Fourth of July holiday, the MSP vendor Kaseya was hit by a huge ransomware attack. The organization behind the attack is REvil, a Russian-linked Ransomware-as-a-Service operation that first surfaced in May 2020. In 2021, they have been attached to a number of high-profile attacks. This breach is still ongoing, but we want to alert our customers to the actions that we have taken at DNSFilter to best secure our customers.
We want to reiterate that if you are a Kaseya customer to follow their advice:
“Our guidance continues to be that users follow Kaseya’s recommendation to shut down VSA servers immediately, to adopt CISA’s mitigation guidance, and to report if you have been affected to the IC3.”
Initial Domain Flagged
At 3:56 p.m. ET on July 2, DNSFilter categorized the first known URL as malware after it was first posted at roughly 3:19 p.m. ET: decoder[dot]re
Prior to our categorization of this domain, there was no traffic to this domain on our network.
Config file with over 1,000 domains disclosed
Early on July 3, a config file was released for the Kaseya attack that included a list of over 1,200 command and control domains. As of 3:58 a.m. ET on July 3, DNSFilter is categorizing all of these domains as malicious.
To ensure you’re protected from these domains sending DNS queries from your system, ensure you have the following DNS threat protection in place (at a minimum) on our network:
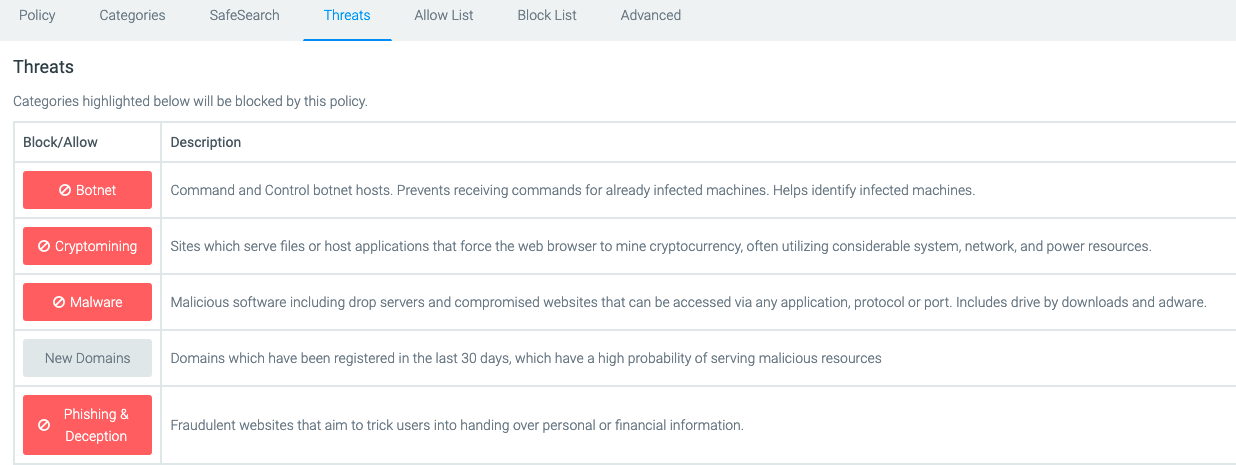
As more information is released or we have additional updates related to actions we are taking at DNSFilter to protect our customers, we will update this blog post.
Update on July 9, 2021: We have shared more information about the CNC domains used in the Kaseya ransomware attack.
Share this
 Artificial Intelligence in Cybersecurity
Artificial Intelligence in Cybersecurity
The term “artificial intelligence (AI)” was first coined in 1956. While progress stalled for many years, we can thank IBM for sparking real interest in AI as viable technology: First in 1997 when the computer Deep Blue defeated a chess champion and again in 2011 when Watson won Jeopardy!
 The Mind Games Behind Cyber Attacks
The Mind Games Behind Cyber Attacks
Hackers have long understood that the most sophisticated firewall is no match for a well-placed psychological trick. While many focus on the technical prowess of cybercriminals, the real magic often lies in their ability to manipulate human behavior. By exploiting our natural tendencies and cognitive biases, hackers can slip past even the most robust security systems. It's not just about cracking codes; it's about cracking the human psyche.
 AI and Cybersecurity Risks: Why DNS Filtering is Critical for AI-Driven Workplaces
AI and Cybersecurity Risks: Why DNS Filtering is Critical for AI-Driven Workplaces
Artificial intelligence is transforming business operations, automating everything from customer service to data analysis. But with these advancements come new security challenges. AI-driven cyber threats are becoming more sophisticated, enabling attackers to automate phishing campaigns, generate malware, and exfiltrate sensitive data at scale. Without proper safeguards, AI tools can unintentionally leak corporate secrets or connect to malicious ...


