Share this
Say Hello to SSO on DNSFilter
by Aliese Alter on Apr 10, 2022 12:00:00 AM
What is SSO?
Single Sign-On is an authentication protocol that allows users to sign into different software systems using a single identity. This identity is provided by third-party identity providers like Okta, OneLogin, or Azure AD.
The application you’re trying to authenticate with sets up a trust relationship with the identity provider that already has your authentication credentials. A certificate shared by the identity platform and the software you’re trying to access is used to sign identity information being shared by the two systems.
This allows you to use your credentials that have been saved on the identity provider to securely access the software. Below is a diagram that details how SSO works:
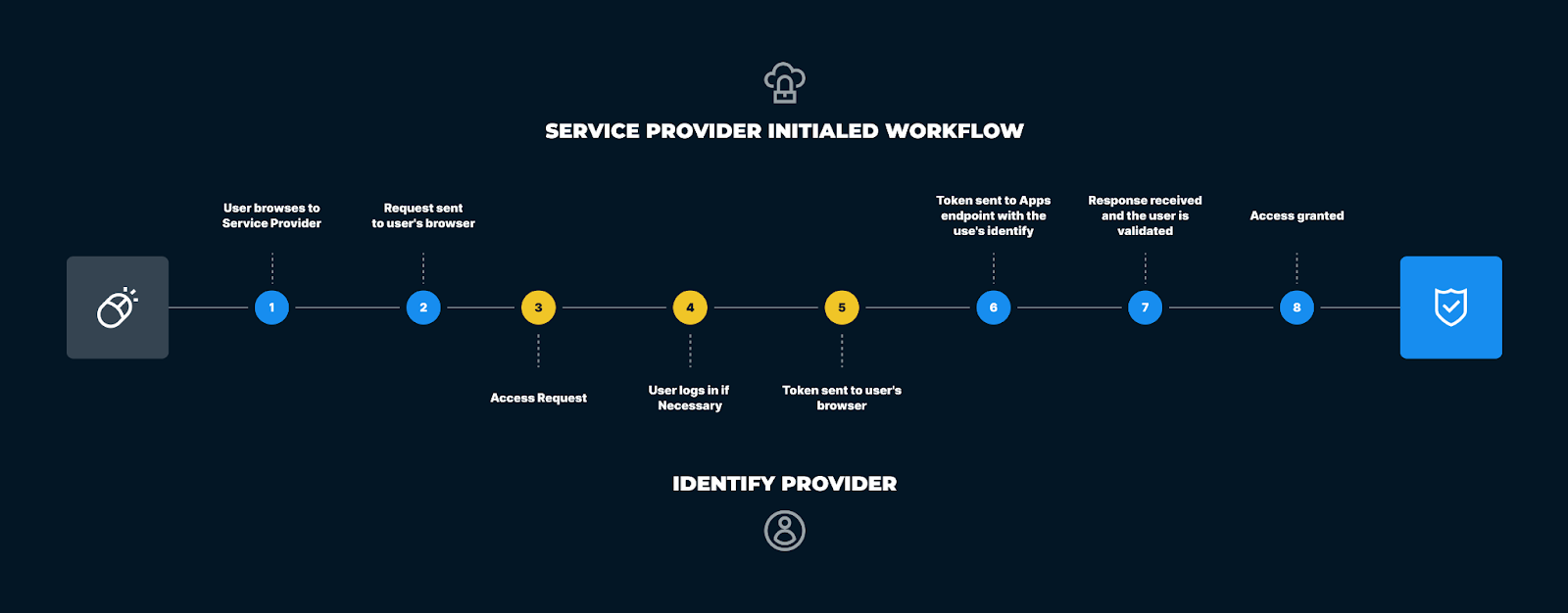
SSO on DNSFilter
DNSFilter customers can now configure Single Sign-On (SSO), enabling dashboard users to securely authenticate with the DNSFilter application.
DNSFilter already makes both threat protection and content filtering easy and affordable. SSO configuration is no different. Customers can optionally control who has access to the DNSFilter application using any Identity Provider (IdP) that supports Generic OpenID (OIDC) protocol, such as Okta and Microsoft Azure Active Directory. DNSFilter has no plans to be featured on the SSO Wall of Shame; so SSO will be offered free of charge to all plans.
How to get started with SSO on DNSFilter
SSO can be configured through the DNSFilter dashboard. Account owners can simply enter their OAuth 2.0 credentials from an IdP in the Single Sign-On section of the Settings page of their DNSFilter account. Once the values have been entered correctly, SSO can be turned on.
For more information on setting up Single Sign-On on your DNSFilter account, checkout the detailed guide on our knowledgebase.
Take advantage of this new functionality today!
Share this
 Artificial Intelligence in Cybersecurity
Artificial Intelligence in Cybersecurity
The term “artificial intelligence (AI)” was first coined in 1956. While progress stalled for many years, we can thank IBM for sparking real interest in AI as viable technology: First in 1997 when the computer Deep Blue defeated a chess champion and again in 2011 when Watson won Jeopardy!
 The Mind Games Behind Cyber Attacks
The Mind Games Behind Cyber Attacks
Hackers have long understood that the most sophisticated firewall is no match for a well-placed psychological trick. While many focus on the technical prowess of cybercriminals, the real magic often lies in their ability to manipulate human behavior. By exploiting our natural tendencies and cognitive biases, hackers can slip past even the most robust security systems. It's not just about cracking codes; it's about cracking the human psyche.
 AI and Cybersecurity Risks: Why DNS Filtering is Critical for AI-Driven Workplaces
AI and Cybersecurity Risks: Why DNS Filtering is Critical for AI-Driven Workplaces
Artificial intelligence is transforming business operations, automating everything from customer service to data analysis. But with these advancements come new security challenges. AI-driven cyber threats are becoming more sophisticated, enabling attackers to automate phishing campaigns, generate malware, and exfiltrate sensitive data at scale. Without proper safeguards, AI tools can unintentionally leak corporate secrets or connect to malicious ...


