Share this
DNSFilter and Twingate announce Zero Trust Network Access
by Tony Huie on Feb 24, 2021 12:00:00 AM
Today we're excited to share our blog with Twingate, a new DNSFilter partner. Twingate was founded with the goal of helping customers easily implement modern Zero Trust Network Access without compromising security or performance. With a product that can be set up in less than 15 minutes and provides a consumer-grade user and admin experience, we believe that “work from anywhere” should just work.
The author of this blog is CEO and Co-founder of Twingate, Tony Huie.
When we started Twingate in 2019, our goal was to modernize the experience of implementing secure remote access, which has traditionally relied on decades-old VPN technology as the foundation. We could never have predicted that the global pandemic of 2020 would accelerate the shift to remote work and further highlight the demand for a truly usable Zero Trust solution. Today, Twingate is announcing the next step in making Zero Trust even more accessible to more organizations, including a partnership with DNSFilter to help fully secure every organization.
Remote work brings new challenges to traditional IP-based networking
Let’s face it—VPNs were never designed for the fully distributed, work-from-anywhere world we live in today. As a result, CIOs, CISOs, and IT administrators find themselves in an uphill battle dealing with the latest security vulnerabilities, managing ever-changing IP allow/block-lists, and grappling with VPN scalability challenges, not to mention needing to provide constant support for user complaints of poor performance, connection reliability, and overall usability. Most often, we encounter customers who come to us disappointed with their existing VPN-based solution after accumulating a patchwork of technologies to support their growth, which have become brittle and difficult to manage over time.
Twingate takes a new approach to trusted access and is focused on building a new foundational primitive for the future of network security: identity. With Twingate, every network connection and packet is tied to a reliable indicator of identity (the user, machine, and/or device) and a robust platform to manage access based on that identity. At Twingate, we believe that over the next 10 years, every company will migrate from perimeter, IP-based security to Zero Trust, identity-first network security.
Twingate and DNSFilter work together to protect your organization
Twingate works by establishing a completely private connection between each client device and only the private resources they are permitted to access within the organization’s protected networks. All other traffic bound for the public internet (e.g. Zoom calls, Google searches) is routed directly to the destination, resulting in highly secure access to private resources without sacrificing connection speed.
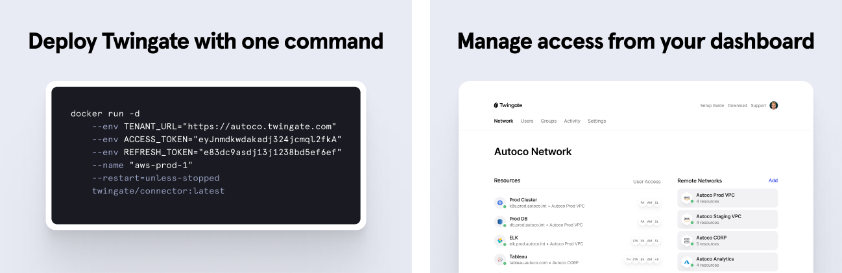
In addition to the benefits of greater security and performance, Twingate can be deployed in minutes, supports every major client platform, provides application-level access controls, and integrates with every major Identity Provider. Administrators can also monitor and maintain their networks through a user-friendly but powerful consumer-grade interface.
One common request we hear from customers at Twingate is that they want a way to also secure all the traffic that flows directly between the user and the public internet. Ransomware and phishing attacks have been on the rise in recent years, which have been further exacerbated by remote work, making DNSFilter the perfect complementary product to Twingate. With DNSFilter’s AI-powered content filtering solution and multi-platform roaming client, admins can now deploy DNSFilter and Twingate side by side to fully protect both private and public user traffic, no matter where they are and what device they’re on.
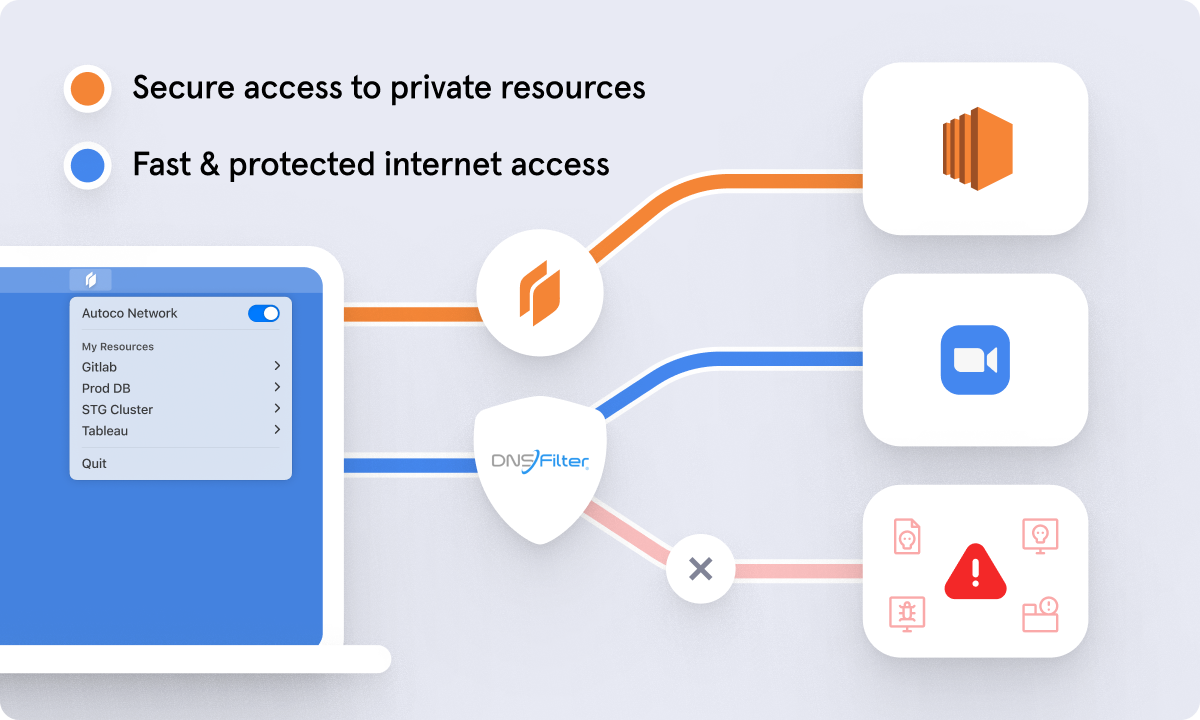
Fast-growing and innovative companies have already adopted forward-looking technologies to enable their globally distributed remote workforces, including modern secure access technologies like DNSFilter and Twingate. For DNSFilter customers currently relying on traditional VPNs, Twingate provides a more secure option that is split tunnel by default—a setting that makes DNS resolution easier to enable. Pairing Twingate with DNSFilter’s Roaming Clients gives IT administrators more granular user access controls. IT teams can share identity-specific access using Twingate and apply filtering policies (and view reports) based on the user with DNSFilter.
Twingate customers report that they often reduce deployment time by 80% and ongoing client setup and support load by 90% compared to their previous VPN, all while expanding their distributed workforces in a more secure way.
By partnering with DNSFilter, Twingate is excited to accelerate the adoption of Zero Trust Network Access and provide true end-to-end threat protection for our customers.
For those who are new to Twingate, please get in touch. We’d be happy to show you around the product via a free product demo.
Share this
 Artificial Intelligence in Cybersecurity
Artificial Intelligence in Cybersecurity
The term “artificial intelligence (AI)” was first coined in 1956. While progress stalled for many years, we can thank IBM for sparking real interest in AI as viable technology: First in 1997 when the computer Deep Blue defeated a chess champion and again in 2011 when Watson won Jeopardy!
 The Mind Games Behind Cyber Attacks
The Mind Games Behind Cyber Attacks
Hackers have long understood that the most sophisticated firewall is no match for a well-placed psychological trick. While many focus on the technical prowess of cybercriminals, the real magic often lies in their ability to manipulate human behavior. By exploiting our natural tendencies and cognitive biases, hackers can slip past even the most robust security systems. It's not just about cracking codes; it's about cracking the human psyche.
 AI and Cybersecurity Risks: Why DNS Filtering is Critical for AI-Driven Workplaces
AI and Cybersecurity Risks: Why DNS Filtering is Critical for AI-Driven Workplaces
Artificial intelligence is transforming business operations, automating everything from customer service to data analysis. But with these advancements come new security challenges. AI-driven cyber threats are becoming more sophisticated, enabling attackers to automate phishing campaigns, generate malware, and exfiltrate sensitive data at scale. Without proper safeguards, AI tools can unintentionally leak corporate secrets or connect to malicious ...


