Share this
You Already Have a Bring Your Own Device Policy: What We've Discovered About How We Now Work
by Serena Raymond on Jan 26, 2022 12:00:00 AM
Bring Your Own Device (BYOD) is a policy in which a company allows users to use their own device (computer, smartphone, tablet) to do company work. With the shift to remote working, company devices are now being used at home more than ever.
Instead of a codified “Bring Your Own Device” policy, that would allow access to company apps and files on an employee’s personal device, we now have the opposite happening: employees are connecting their personal apps and files to their work devices, and using those devices for leisure. Behold, the rise of Bring Your Company Device (BYCD)!
With the move to an entirely distributed workforce that many organizations are experiencing, it shouldn't be surprising that this has happened. Some employees have always used work devices for personal use, even in a traditional office environment. But what is surprising is the increased frequency of users accessing sites generally considered inappropriate for work between 2020 and now.
We looked at over 1 million active company machines (processing roughly 3 billion DNS queries per single day) on our network and saw that the percentage of network traffic to streaming sites grew nearly 300% from February 2020 to February 2021—employees are spending more time than ever watching streaming content at work.
We also noticed a peculiar pattern of when users were looking at streaming content and other sites.
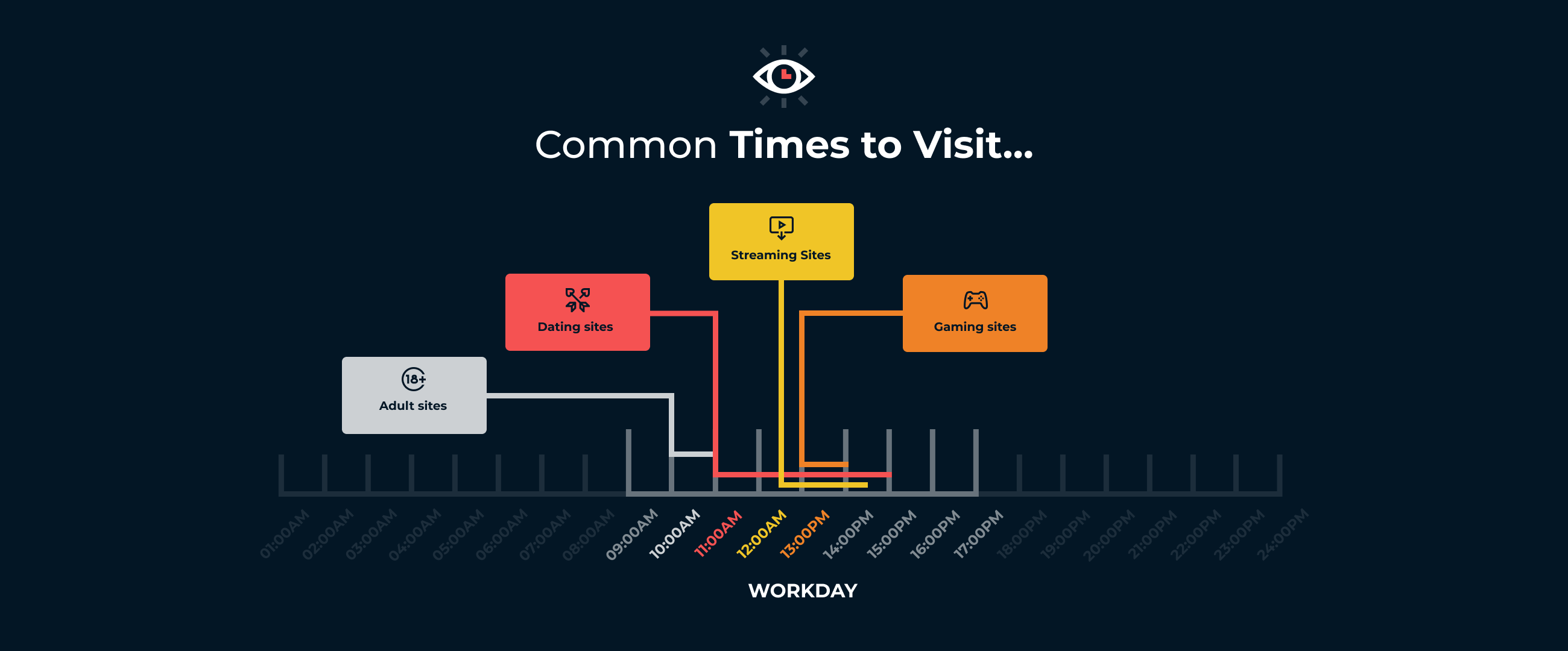
Starting at 10 a.m., that's when users were most likely to visit adult content on work devices. An hour later, at 11 a.m., was the most frequent time of day for them to check out dating sites. By 12:30 (and for roughly the length of 2-hour movie), users were more likely to view streaming. And at 1 p.m. is when gaming sites were most-often visited.
Traffic to dating sites also grew 59% between 2020 and 2021.
Interestingly, though social media is a known time-waster, only 10% of businesses on our network are blocking social media access to their employees. Our customers are most likely to block Snapchat (9.6% blocked) or Instagram (5.9% blocked). Twitter, Facebook, and TikTok are all blocked on our network at nearly the same rate, between 3.4% and 3.9% (respectively). When we polled our employees internally asking them which social sites were most blocked on our network, the most common answer was Facebook.
Finally, when it comes to cybersecurity, we were able to determine a pattern between the successful identification of a phishing scam between users who were using their company devices during work hours, or during leisure time. Employees using such devices during work correctly flag sites as phishing 90% of the time. But users are nearly 40% less likely to correctly flag phishing sites when browsing during their leisure time. It seems that context is everything.
Although the concept of BYOD has been around for years, it has been flipped on its head. Your company-owned device is now doing double duty in the off hours. This creates additional security risk because of shadow IT applications, visits to risky websites, and filesharing occurring off-network. Blending work and pleasure on a single device is here to stay, but make sure your cybersecurity accounts for the myriad of ways in which each device will be used, not just usage in a 9-5 work context.
A content filtering tool that gives you the ability to schedule policies for certain times can greatly increase productivity and lower your cybersecurity vulnerability by locking down visits to high-risk sites, and keeping users off time wasters. Get a free trial of DNSFilter.
Share this
Categories
- Featured (267)
- Protective DNS (23)
- IT (15)
- IndyCar (9)
- Content Filtering (8)
- AI (7)
- Cybersecurity Brief (7)
- IT Challenges (7)
- Public Wi-Fi (7)
- Deep Dive (6)
- Malware (4)
- Roaming Client (4)
- Team (4)
- Compare (3)
- MSP (3)
- Machine Learning (3)
- Phishing (3)
- Ransomware (3)
- Tech (3)
- Anycast (2)
- Events (2)
- Staying Ahead of Cyber Threats (2)
- Tech Stack (2)
- Secure Web Gateway (1)
 The DNS-Based Threats Your Firewall Ignores
The DNS-Based Threats Your Firewall Ignores
Your firewall is working hard… but not smart. And cybercriminals love that.
Like a bouncer at the club with a clipboard—great at stopping the obvious troublemakers that aren’t on the list, but completely oblivious to unknown threats. They excel at blocking unauthorized access through known ports and protocols, but they often overlook a critical vulnerability: DNS traffic and what’s on the other side of a link. This oversight allows cybercrimina...
 AI vs AI: Using DNS to Combat Sophisticated Cyberattacks
AI vs AI: Using DNS to Combat Sophisticated Cyberattacks
Introduction: The AI Cybersecurity Arms Race
Artificial intelligence (AI) has transformed the cybersecurity landscape—both for defenders and attackers. While AI-powered cybersecurity solutions offer advanced threat detection, AI-driven cybercrime is evolving at an alarming rate, automating attacks that are more sophisticated, evasive, and dangerous.
 How DNSFilter Stops Zero-Day Attacks: The Invisible Threat Costing Businesses Millions
How DNSFilter Stops Zero-Day Attacks: The Invisible Threat Costing Businesses Millions
Imagine waking up to find your company's most sensitive data exposed, your systems locked, and your reputation in tatters. This nightmare scenario isn't just a hypothetical—it's the reality for businesses falling victim to zero-day attacks. In 2021, four zero-day exploits targeting Microsoft Exchange servers affected over 250,000 organizations worldwide, leaving countless systems vulnerable to data theft and ransomware.


