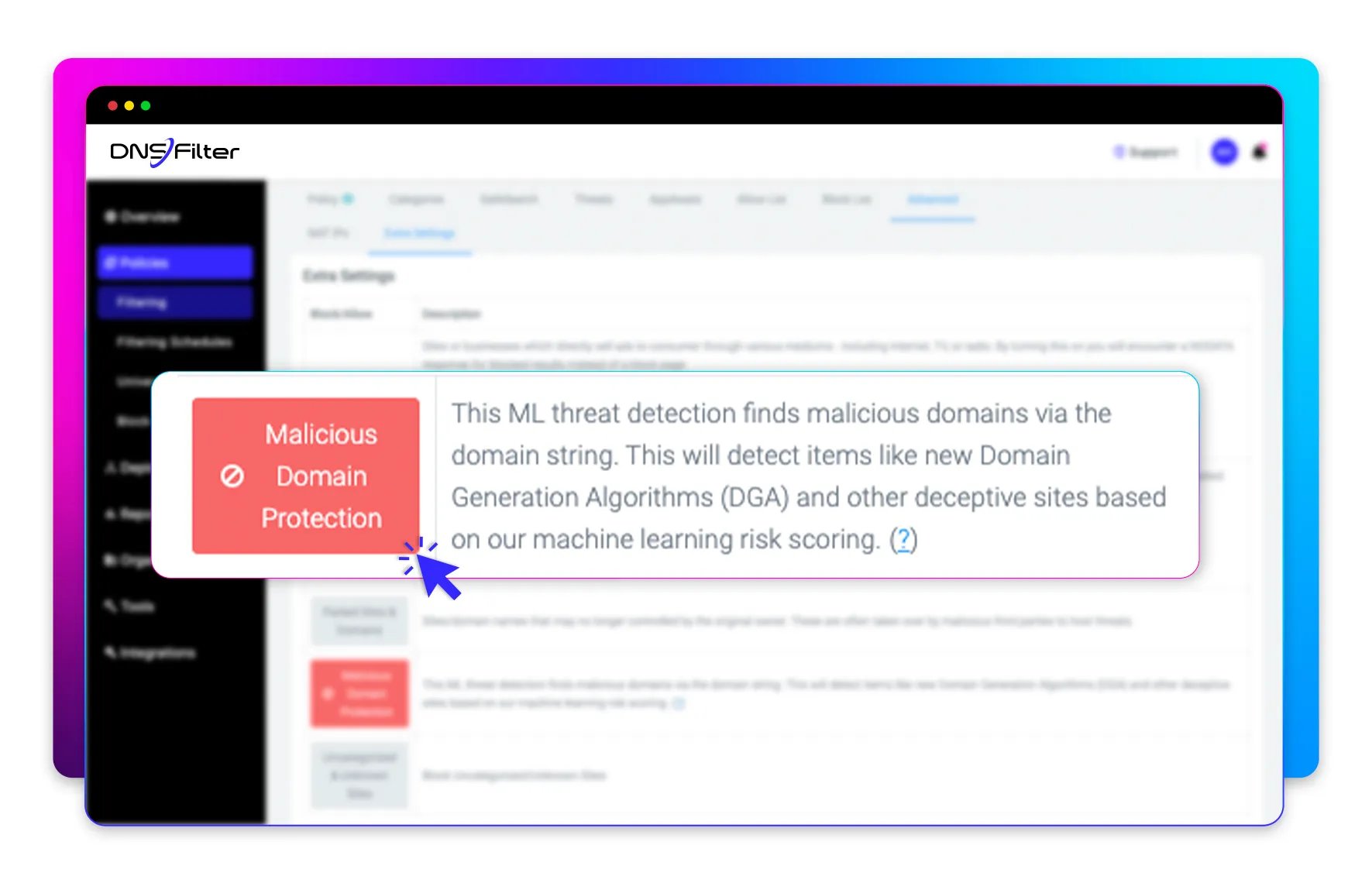
How it works
Malicious Domain Protection uses machine learning to analyze DNS queries to assess whether they are likely to be associated with a malicious host.
By analyzing the DNS query, attempted connections to likely malicious domains are blocked, providing a first-line defense to protect users and corporate networks.
Enabling malicious domain protection is simple
Watch the video to see how easy it is to setup and configure a policy to block threats using Malicious Domain Protection.
Training the machine learning model
To train a machine learning classifier, training data is needed. DNSFilter's data scientists had access to the world's fastest Dual-Anycast resolvers that process over 89 billion DNS queries daily for over 30 million users.
Over 35 million daily DNS queries are identified as threats and blocked, before they ever resolve to a client machine. Malicious Domain Protection's classifier was trained and fine-tuned using over 16 million queries, a mix of both known good and known bad domains contributing to a highly accurate machine learning model.
More threats and faster detection
During testing, Malicious Domain Protection detected 7,000 risky domains that were not yet identified by any threat intelligence feeds. Threats were identified up to 10 days ahead of third-party threat feeds, with one domain being caught 59 days ahead.
.webp?width=699&height=450&name=Updated%20Homepage%20Images_Insights%20Reporting%20(1).webp)
The threats we face
Unknown malicious domains seen in the wild can be used with malware, botnets, phishing attacks or command-and-control servers.
Attackers use the period before their domain is discovered to launch attacks that go undetected by firewalls, IDS, and other threat detections that rely on threat feeds or other information.
Some malware families algorithmically generate upwards of 250,000 unique domains. Also known as DGAs, these domains are often the first signs of malware, spambots, phishing, and cryptojacking, and more.
Recommended reading:
1.webp?width=1300&height=500&name=image(3)1.webp)
Protective DNS and DNS Security: What's the Difference?
Customers love us, threats hate us







.png?width=154&height=50&name=fresno%20(1).png)













1.webp?width=1300&height=500&name=aboutmaliciousdomainprotectionblogimage(1)1.webp)
