Share this
Artificial Intelligence in Cybersecurity
by Serena Raymond on Apr 8, 2025 3:30:00 PM
The term “artificial intelligence (AI)” was first coined in 1956. While progress stalled for many years, we can thank IBM for sparking real interest in AI as viable technology: First in 1997 when the computer Deep Blue defeated a chess champion and again in 2011 when Watson won Jeopardy!
Since 2020, artificial intelligence has rapidly evolved from a futuristic concept into a foundational element of every organization’s information technology and cybersecurity infrastructures. Today’s AI systems can analyze data at scale, detect novel threats in real time, and adapt quickly to an ever-changing threat landscape—capabilities that are increasingly critical as cyberattacks become more sophisticated.
At the core of most AI-driven cybersecurity tools is machine learning (ML)—a subset of AI that enables systems to learn from data and improve over time without being explicitly programmed. ML allows our technology at DNSFilter to detect patterns, flag anomalies, and identify malicious domains that static, rule-based systems would miss.
By combining AI and machine learning, DNSFilter is able to identify deceptive domains in real time, keeping users safe from threats that evolve faster than any human-curated list could track.
How Machine Learning Powers AI in Cybersecurity
Artificial intelligence is when we give a machine the ability to perform tasks that are traditionally done by humans. While that can cover a wide range of applications, the type of artificial intelligence we want to focus on when talking about cybersecurity is related to machine learning.
Machine learning is the method by which an AI learns. An AI will use machine learning to identify patterns and make decisions, with varying degrees of human supervision.
How does artificial intelligence work?
While machine learning can work in a variety of different ways and the steps can be complicated, this is the general process:
- The AI is programmed to perform a task or goal (e.g., detecting malicious websites)
- The AI is given the data necessary to perform its task, the larger the data set the better (e.g., examples of malicious sites and benign sites)
- The AI performs the task it was programmed to do based on the data it was trained with. Making prediction based on the patterns it has learned
- The user(s) will judge the AI on how well it performed that task. The machine learns and adjusts its output based on the the evaluation it receives
- Based on how well it performed the task, the AI comes away with new learnings, improving how it can detect new patterns and solve problems (like identifying never-before seen threats)
A great example of this is an AI tasked to create a picture of a hamburger. It’s given thousands of pictures of cheeseburgers so it understands what a hamburger generally looks like. It then creates a picture of a cheeseburger, repeatedly.
Here’s what it looks like when an AI learns how to make a hamburger:

We’re not joking, none of those were real hamburgers. They were all AI generated.
Within an AI, there are essentially two brains: The brain that learns and does the work, and the brain that takes in the data and judges the work. These two brains speak to one another after a task is complete (or after a picture of a cheeseburger is generated).
The AI will do whatever it can to make the task it performs closely match the examples it was given.
The part of the AI meant to judge its own work might look at those pictures of hamburgers and recommend making the burgers look a little less messy if it thinks that will make them match the original data better.
The Role of AI in Cybersecurity
AI’s integration into cybersecurity has transformed how organizations identify and mitigate threats. According to IBM’s 2024 Cost of a Data Breach Report, businesses using AI-driven security tools reduced breach detection times by 63% compared to manual methods. Key applications of AI in cybersecurity include:
| Real-Time Threat Detection: Machine learning algorithms analyze network traffic patterns to identify anomalies like unauthorized API calls or unusual data exfiltration volumes. | Automated Incident Response: AI resolves a majority of low-level alerts without human intervention, freeing analysts to focus on critical threats. | Enhanced Zero Trust Architecture (ZTA): AI evaluates user behavior and device health in real time to enforce dynamic access controls. |
DNSFilter’s AI doesn’t just detect malicious domains—it blocks them in real time, often before they're even reported elsewhere. Explore our malicious domain protection capabilities to see how we keep users safe without slowing them down.
AI in Action
By embracing artificial intelligence in cybersecurity, companies can improve their systems more rapidly. DNSFilter’s machine learning algorithm allows us to continuously increase the number of malicious sites detected on a daily basis as opposed to relying on static, human-generated lists of malicious sites.
There were approximately 362.4 million new domain name registrations across all top-level domains (TLDs) in the first quarter of 2024. That’s roughly 28,000 new domains per day!
If you only rely on lists of malicious sites curated by humans, do you think you’d be able to keep up with categorizing 28,000 new domains every day? That’s a job for AI.
DNSFilter’s AI is purpose-built to scale with today’s threat landscape—identifying brand-new domains before they’re weaponized. For example, over a six month period we detected that potentially risky new domain traffic more than doubled.
Let’s take a look at some of the sites our AI has categorized as deceptive.
⚠️Compromised websites
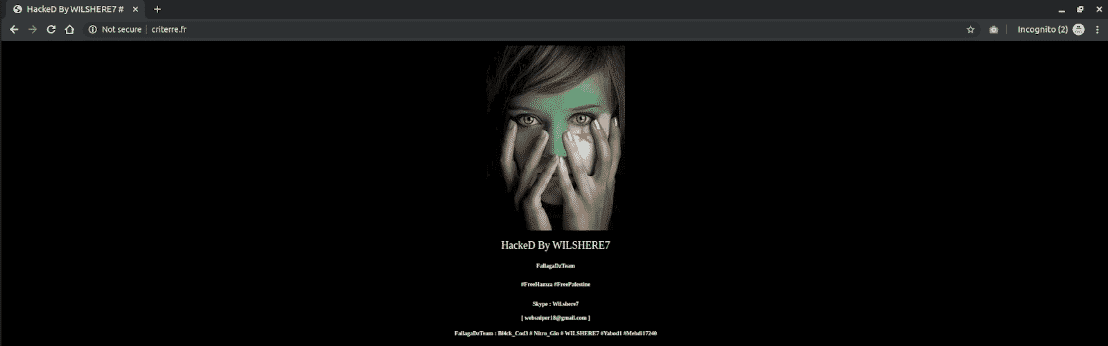
A website that’s compromised is one that a black hat hacker has taken over. Hackers will take down the original site, stripping out all of its original content, and rebrand the site as their own with a message.
This frequently occurs on WordPress sites that are not configured correctly and are easy to infiltrate.
Some of the more famous instances of websites being compromised were done by the group Anonymous, who have vandalized a large number of websites since the late 2000s.
These sites are dangerous because hackers may decide to infect the site with malware or forced downloads that might be transferred to a visitor of the site.
Malware and AI in 2025
And while compromised sites remain a major risk, the tactics behind them have evolved. In 2025, we’re seeing malware campaigns that not only hide behind these takeovers but are enhanced by AI—delivering faster, smarter, and more evasive threats than ever before.
AI-Powered Malware Distribution
Today, attackers use AI to mutate malware on the fly, automatically rewriting code to evade traditional signature-based detection. These adaptive threats are often distributed via new, quickly registered domains—making real-time AI detection at the DNS layer critical.
⚠️Credential phishing
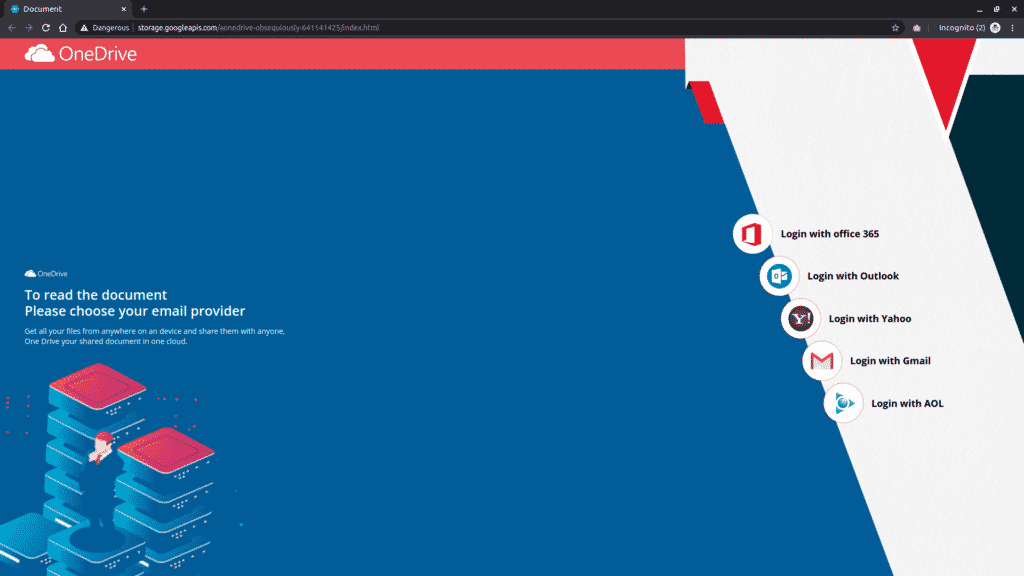
Phishing occurs when someone attempts to gain unauthorized access to someone’s account, usually in an effort to steal their money. One of the more common phishing sites hackers set up are pages that mimic a company login page that someone might use daily, like Gmail or Office 365.
In the example above, our AI caught a deceptive page that was meant to trick the user into thinking it is their OneDrive account. This method is particularly misleading as not only does the page provide five options for a person to enter personal credentials, but the URL is set up on a Google APIs site. Because this is a legitimate domain, some machine learning algorithms, and certainly many static lists, would miss this deceptive site altogether.
AI Phishing and Credential Harvesting in 2025
This new wave of phishing doesn’t stop at fake login pages. With generative AI, attackers are now fabricating voices, faces, and full conversations to manipulate victims—making deepfakes a real and rising threat in credential theft.
Deepfake Phishing
Deepfakes are no longer just a novelty. AI-generated audio and video can convincingly impersonate executives, tricking employees into approving fraudulent transactions or revealing sensitive credentials. DNSFilter’s AI can flag the domains hosting these spoofed portals and phishing landing pages.
AI-Generated Credential Harvesting Kits
Credential phishing has evolved as well. Adversaries are using AI to generate highly-targeted phishing kits, customizing login pages with dynamic content based on the victim’s industry, geography, or recently breached services. Some of these have even been configured to bypass two-factor authentication (2FA).
DNSFilter’s AI can recognize the patterns and infrastructure associated with these kits—even if the content looks original
⚠️Templates and Spam Pages

If you look closely at the image above, you’ll notice something strange. This isn’t a completed website. This is just a template. If you were able to click on the page, the links don’t go anywhere and the text is just nonsense.
Why is this a problem?
Template sites, or boilerplate sites, are set up to mimic a new webpage and will have some type of malware hidden on a link within the site. You won’t find anything inherently wrong on the homepage of this site, but the deeper you get the more likely you are to stumble onto something malicious.
A human combing through sites might miss that this site is deceptive. Luckily, our well-trained AI caught this one before our customers became affected.
Malicious Spam and AI Scam Templates in 2025
While spam templates are a quick and easy way to fool users, generative AI takes them further—automatically building out full scam sites that look polished, legit, and dangerously convincing at first glance.
Generative AI Scam Pages
Attackers are now using generative AI to spin up convincing scam websites and fake login pages, complete with copy, branding, and even dynamic chatbots. These pages look increasingly real and can appear on legitimate hosting services or hijacked subdomains, making detection difficult without AI-powered behavioral analysis.
What does this mean for you?
At DNSFilter, we’re regularly training and perfecting our AI to notice new types of deceptive sites that haven’t been reported anywhere else before. We’re creating intelligent systems that block 200 million threat queries each day, and we’re doing it before your systems are compromised, instead of after. That means we find them first, before our customers ever know they’re there.
Find out how you can start relying on artificial intelligence in cybersecurity and start your free trial of DNSFilter today.
This article was originally published on February 11, 2020. It was updated on April 8, 2025 to include more recent statistics and information about DNSFilter’s capabilities.
Share this
 Artificial Intelligence in Cybersecurity
Artificial Intelligence in Cybersecurity
The term “artificial intelligence (AI)” was first coined in 1956. While progress stalled for many years, we can thank IBM for sparking real interest in AI as viable technology: First in 1997 when the computer Deep Blue defeated a chess champion and again in 2011 when Watson won Jeopardy!
 The Mind Games Behind Cyber Attacks
The Mind Games Behind Cyber Attacks
Hackers have long understood that the most sophisticated firewall is no match for a well-placed psychological trick. While many focus on the technical prowess of cybercriminals, the real magic often lies in their ability to manipulate human behavior. By exploiting our natural tendencies and cognitive biases, hackers can slip past even the most robust security systems. It's not just about cracking codes; it's about cracking the human psyche.
 AI and Cybersecurity Risks: Why DNS Filtering is Critical for AI-Driven Workplaces
AI and Cybersecurity Risks: Why DNS Filtering is Critical for AI-Driven Workplaces
Artificial intelligence is transforming business operations, automating everything from customer service to data analysis. But with these advancements come new security challenges. AI-driven cyber threats are becoming more sophisticated, enabling attackers to automate phishing campaigns, generate malware, and exfiltrate sensitive data at scale. Without proper safeguards, AI tools can unintentionally leak corporate secrets or connect to malicious ...


